[citation needed]Mw2 level 70 hack mac Would probably be best to bring it up on their forums.. Bluetooth Hacking ToolsFeb 24, 2020 This wikiHow teaches you how to install and use the Super Bluetooth Hack Java file on an Android phone.. This hciconfig is the main Linux command line utility used for interacting with Bluetooth device (Bluetooth dongle).
[1] The remaining 24 bits have approximately 16 8 million possible combinations, requiring an average of 8.
bluetooth hacking tools
bluetooth hacking tools, bluetooth hacking tools kali, bluetooth hacking tools apk, bluetooth hacking tools github, bluetooth hacking tools windows, bluetooth hacking tools termux, bluetooth hacking tools linux, bluetooth hacking tools for iphone, bluetooth hacking tools for pc, bluetooth hacking tools 2020 Nexus 2 Vst Crack Download
Regardless - To the OP Current mobile software generally must allow a connection using a temporary state initiated by the user in order to be 'paired' with another device to copy content.. Both Bluesnarfing and Bluejacking exploit others' Bluetooth connections without their knowledge.. There seem to have been, in the past, available reports of phones being Bluesnarfed without pairing being explicitly allowed.. Super Bluetooth Hack is designed to allow you to see and edit files on a Bluetooth-connected Android smartphone.. [citation needed] This allows access to calendars, contact lists, emails and text messages, and on some phones, users can copy pictures and private videos. Glibc Install-symbolic-link Segmentation Fault
bluetooth hacking tools apk

bluetooth hacking tools windows
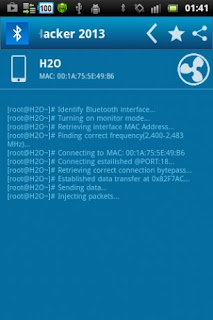
It is just an xbox port and they assumed everyone would have the same hardware anyway.. By turning off this feature, the potential victim can be safer from the possibility of being Bluesnarfed; although a device that is set to 'hidden' may be Bluesnarfable by guessing the device's MAC address via a brute force attack.. Bluetooth uses a 48-bit unique MAC Address, of which the first 24 bits are common to a manufacturer.. 4 million attempts to guess by brute force. Depending on your direction, there are a different set of tools you should use Therefore, concentrating on the reconnaissance (discovery phase) and internal kali Bluetooth hacking tools would be our goal for this chapter.. While Bluejacking is essentially harmless as it only transmits data to the target device, Bluesnarfing is the theft of information from the target device.. After the disclosure of this vulnerability, vendors of mobile phone patched their Bluetooth implementations and, at the time of writing[when?], no current phone models are known to be vulnerable to this attack.. As with all brute force attacks, the main obstacle to this approach is the sheer number of possible MAC addresses. 518b7cbc7d


0